Protect Your Privacy Online: a Complete Guide to Apps and Best Practices

Billions of dollars are being stolen each year, so how do you protect yourself against the threats to your online security?
We live in a time with more awareness, more techniques, and more tools for staying safe online than ever before. Yet last year in 2017, there were 16.7 million victims of identity fraud in the U.S. alone, according to a study by Javelin Security. That’s 1.3 million victims more than in 2016, and amounts to $16.8 billion dollars being stolen — an average of around $1000 dollars per person. Most of the time, fraud costs you a couple of dollars, amounts that the fraudulent companies think consumers won’t notice or check. At worst, you could find your accounts completely maxed out before you have time to retaliate. As if this isn’t bad enough, everyone is gathering data on us through ads, trackers, cookies. Our footsteps across the web are emblazoned clearly, for all companies to see.
We’re living in the most complex era for fraud and privacy prevention, and the technological advances constantly taking place around us are only increasing this complexity. The question is, how do we protect ourselves from trackers, hackers, and those collecting data? This month at Timing we’ve been focusing on privacy, starting with our article specifically about time tracking apps and privacy. We’re kicking it up a notch this comprehensive guide to protecting your data when using the internet. With the minefield of misinformation out there, this guide aims to simplify things and bring you only the facts.

Protect your privacy from trackers
The adage goes, “If you’re not paying for a service, you’re the product, not the customer.” Although it’s cynical, it’s never been more true. If a service is being offered for free, then they’ll be making their money elsewhere — probably by selling your information. So how do you stop this happening? If you’re a Chrome user, then there are some great extensions and add-ons to help you discover which sites are sending information to third party sites, and stop them from doing so. Some of the best are Ghostery, which blocks invisible tracking cookies and plug-ins, and AdBlock Plus.
It’s also necessary to create healthy habits around internet use — something that goes further than just wiping your browser history. Safari is far better equipped than Chrome to stop trackers, which means that splitting your time between the two browsers can help protect you. A good practice is to use one browser for social sites, which are high-risk sites for privacy and data concerns, and another for emails and bank details — so any online purchases.
Be careful which extensions you install on Chrome, too. While extensions can be fun and useful, it’s not uncommon for even high-security ones to be compromised. For instance, OneLogin suffered a breach last year which enabled encrypted data to be read. If malware enters through an extension and gains access to your passwords, then it’s game over — another reason to separate banking and email details from social sites.
‘Why should I care?’
If this is a statement you’ve heard yourself say, then you’re not alone. Privacy has become relative, as oversharing is now the norm. Go back to the 50s, and tell people that in 2018 we post to over 1000 ‘friends’ about our love lives, eating habits and political opinions. They’d think we had gone mad. Not caring where your personal information goes is not only naive: it’s dangerous. Companies make profitable businesses from selling your personal information — so who’s buying?
Your data isn’t just being used to target ads specifically to your interests. The government is keeping information about you, as are organizations such as the IRS. Anything your reveal online about taxes and income can now be tracked back to you. Medical insurers have access to your lifestyle, and can up your premiums. Even if you still don’t feel you personally need to be concerned about the amount of information stored against you, privacy can be the difference between life or death for some — political refugees, LGBT community, or public figures. Don’t they deserve a less casual attitude towards data storage?

What’s really the best way to password protect?
Everyone knows the usual stock phrases about passwords, and what to and not to-do. Don’t use personal information, don’t use the same password, don’t use simple to guess formulas … but how careful are you really with this? Unfortunately, humans are remarkably predictable with their passwords, meaning that it’s easy for a computer program to crack. This means that even if you’re relatively rigorous at creating ‘strong’ passwords as ranked by form fills, you’re probably using a crackable formula simply because you’re human.
For example, take the word ‘password’. It’s a terrible password (yet still commonly used, for some mysterious reason). Now add in the elements required by form fills to make it ‘strong’. Mixed case, numbers, and something to stop it being a dictionary word. Is ‘PassW0rd123’ really any stronger? How many passwords do you have like this? Thanks to common substitutions, any computer program and potential identity thief will be well aware of needing to vary the letters of dictionary words with obvious numbers. This means that passwords such as “vuln3rabl3” or “trustno1” are safer than an all-letter password, but still crackable. In fact, SplashData ranked the latter as one of the 25 worst commonly used passwords back in 2014.
Depending on the power of the computer being used, a modern computer takes about two days to crack an eight-character password that is all lowercase (since there are 26^8, or 208,827,064,576 possible combinations). A large botnet of the sort used by hackers, though, can crack the code in 1.8 seconds. The more combinations you can create — meaning the longer and more complex the password — the longer it will take to crack.
Passphrases are a good solution to creating longer passwords, but the trick is to make them completely random, and to include a minimum of four words. While this might seem simpler (and more crackable) to you, as they make more sense, in reality they’re both easier for you to remember and harder for a computer to crack. This is explained in a comic by XKCD:
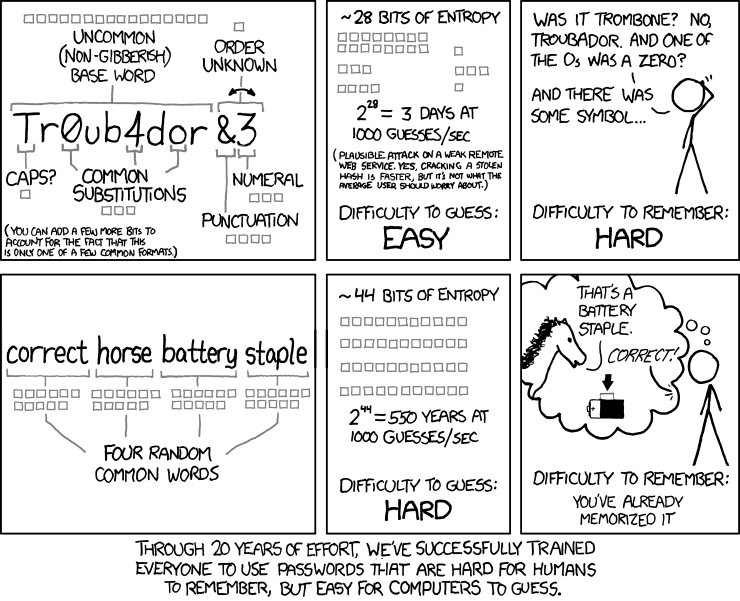
Comic from https://xkcd.com/936/
How do I remember these longer passwords?
If you’ve become rigorous about never using the same password twice, then you’ll almost certainly be wondering how on earth you’re going to remember all these passwords. Password managers have got a bit of a bad rap recently after Lastpass experienced a breach in security, but that should be no reason not to use them. At the end of the day, the technology that password managers are using to keep your passwords safe are still miles ahead of anything you could create yourself.
Setting up two-factor-authentication can be the extra precaution needed to make you feel safe and secure in your password management software. If you select a tool with a password generator then you can become one of the few who don’t reuse passwords (password-repeaters being a shocking 87% of under 31s, and 81% of over!). Just make sure you remember your master password. Of course, if you have an iPhone, then you’ll have the extra security of touch or face ID.

Be mindful of the apps you install, including time tracking apps
There seems to be the assumption that if an app is on the App store, then it’s safe. But with well over two million apps in Apple’s App Store alone, that’s an awful lot of developers you’re trusting to stay up to date with security protocols. According to a survey done in 2015, 90% of all apps had at least 2/10 OWASP (Open Web Application Security Project) risks. This ranges from insecure data storage to unintended data leakage. If an app is hacked or compromised, it’s your data that is vulnerable.
Before you download any app, check that it’s from a credible developer with a privacy policy. It’s also worth checking where your data is stored. Is it stored locally, or uploaded to their servers? A lot of the time, we can forget that our phones store as much important data as our laptops. It’s easy to download apps without thinking about it — or if we have children, often they can download games or similar apps that compromise our security. This can be easily navigated by requiring a password to download apps.
Apps that screenshot can also be a risk to your data, as they could be taking pictures of your personal information that are then stored on the web. At present, there’s a loophole in Apple security that allows even sandboxed Mac apps to take screenshots. When choosing an app that’s recording any sort of personal data, such as a time tracking app, make sure that you check what is happening with the data.

Arm yourself against attackers by being two steps ahead
If your device does get stolen, it’s important to make sure you have all the precautions taken to make sure your data doesn’t get into the wrong hands. Make sure you have Find My Phone or remote location enabled in case your phone gets lost or stolen. If you have an Apple device, there’s a series of actions you can follow to keep your data safe. Changing passwords, setting your device to lost mode, and using Find My Phone to track it can all help stop thieves accessing your personal information.
Setting up content filters, even if you don’t have children you don’t want accessing certain parts of the internet, is another important precaution to take when you first set up your device. Most of the time, people don’t mean to visit sites which pose a security threat — which is why filtering them out is important to avoid anything being accidentally downloaded onto your laptop.
Stay up to date with downloads
Often developers solve any bugs and issues which might cause a security breach in their updates, so it’s important to keep up with all the latest downloads and most recent operating systems. In particular, make sure your anti-virus software is always updated to the latest version. Although it might seem like your update notifications are constantly full, making sure you check and deal with them regularly will pay off in the long run … quite literally, if it keeps you from having money stolen.

Take Extra Precautions When Sharing Any Data
What would you say if I told you that one of the times when you’re most vulnerable to identity fraud is when you’re filing your tax return? And you didn’t think taxes could be any less pleasant? It’s a myth that hackers need all your credit card details to steal your identity, and consequently your money. They can use a variety of identity data, as long as it relates to your identity. With Social Security numbers and passwords they can file fraudulent tax returns. While they pocket the refunds, you end up trying to explain what’s happened to the authorities.
To avoid data breaches, make sure you’re extremely careful when sharing data, no matter how much you trust the other person. Certain password managers allow you to securely share your passwords, and then revoke access afterwards, without ever giving the password itself away. This means your accountant can access your information, without having to know your password.
Speaking of data sharing, make sure you keep your laptop as secure as possible at all times. This means disabling bluetooth when you’re not using it, staying off secure networks, and keeping all your devices locked with passcodes.
Keeping your privacy online can seem complicated and overwhelming, but once you’re properly informed about how to stay safe you can implement habits to protect yourself from hackers and thieves. If you’re in the EU, the new GDPR laws are sure to help you feel safer, as there will be far stricter laws around companies storing your data. Regardless of where you are, being careful about tracking cookies and what data is available about you — especially through the use of social media sites — is an important practice and should be part of your online routine. No matter how invisible you think you are, being forgotten is more complicated than simply emptying your data cache.
Want a time tracking app that values both detail and accuracy, and privacy? Download a free trial of Timing today.
